The Evolving Landscape of Espionage: Spy Trends 2025
Related Articles: The Evolving Landscape of Espionage: Spy Trends 2025
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to The Evolving Landscape of Espionage: Spy Trends 2025. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
The Evolving Landscape of Espionage: Spy Trends 2025

The world of espionage is a dynamic and ever-changing landscape, driven by technological advancements, evolving geopolitical realities, and the constant pursuit of information. As we look towards 2025, several key trends are shaping the future of intelligence gathering and covert operations. Understanding these trends is crucial for governments, businesses, and individuals alike, as they offer insights into the evolving nature of threats and opportunities in the digital age.
1. The Rise of Cyberespionage:
The digital revolution has fundamentally transformed the nature of espionage. Cyberespionage, the use of computers and networks to gather intelligence, has become a dominant force, surpassing traditional methods in both its scope and impact. This trend is expected to continue, with sophisticated cyberattacks becoming more common and targeting critical infrastructure, financial institutions, and government agencies.
Key Aspects of Cyberespionage in 2025:
- Advanced Persistent Threats (APTs): Nation-state actors will leverage advanced persistent threats (APTs) to gain long-term, covert access to target systems, often exploiting vulnerabilities in software and network infrastructure.
- Artificial Intelligence (AI) in Cyberespionage: AI will play an increasingly significant role in cyberespionage, automating tasks such as target identification, vulnerability analysis, and attack execution.
- Exploitation of Internet of Things (IoT) Devices: The proliferation of IoT devices creates vast opportunities for cyberespionage, as these devices are often poorly secured and can be compromised to provide access to sensitive data and networks.
- Data Breaches and Exfiltration: Cyberespionage will focus on stealing large volumes of data, including sensitive personal information, trade secrets, and military intelligence, using sophisticated techniques to exfiltrate data without detection.
2. The Convergence of Physical and Cyber Espionage:
The lines between physical and cyber espionage are blurring as the two domains become increasingly interconnected. This convergence will manifest in hybrid attacks, where cyber operations are used to facilitate physical espionage, or vice versa.
Examples of Convergence:
- Cyber-enabled Surveillance: Cyberattacks can be used to remotely activate surveillance devices, such as cameras and microphones, providing real-time intelligence on physical locations.
- Physical Access through Cyber Means: Cyberattacks can be used to disable security systems, granting physical access to buildings and facilities.
- Targeted Disinformation Campaigns: Cyber operations can be used to spread disinformation and manipulate public opinion, potentially influencing political outcomes and social unrest.
3. The Importance of Human Intelligence (HUMINT):
Despite the rise of cyberespionage, human intelligence (HUMINT) remains a critical component of intelligence gathering. While technology provides access to vast amounts of data, it is human analysts who interpret and contextualize that data, making it actionable intelligence.
The Value of HUMINT in 2025:
- Building Relationships and Trust: HUMINT relies on building relationships and cultivating trust with individuals who possess valuable information.
- Gaining Context and Deeper Understanding: Human analysts can provide context and deeper understanding to data gathered through cyber means, identifying patterns and connections that might otherwise be missed.
- Uncovering Hidden Information: HUMINT can uncover information that is not readily available online, such as sensitive conversations, secret meetings, and internal decision-making processes.
4. The Growing Role of Open Source Intelligence (OSINT):
Open source intelligence (OSINT) refers to the collection and analysis of publicly available information. This trend is driven by the increasing volume of data available online, making it a valuable resource for intelligence gathering.
Key Aspects of OSINT in 2025:
- Social Media Analysis: Social media platforms provide a wealth of information, including user profiles, posts, and interactions, which can be analyzed to understand individuals, organizations, and events.
- Data Mining and Analysis: Sophisticated tools and techniques will be used to analyze large datasets from various sources, including news articles, government reports, and academic publications.
- Geospatial Intelligence (GEOINT): Satellite imagery, aerial photography, and mapping data can be used to analyze physical locations and identify potential targets or threats.
5. The Rise of Private Intelligence Firms:
Private intelligence firms are increasingly playing a role in espionage, offering their services to governments, businesses, and individuals. These firms leverage advanced technology and expertise to provide intelligence gathering, risk assessment, and security services.
Benefits of Private Intelligence Firms:
- Specialized Expertise: Private intelligence firms often have specialized expertise in specific areas, such as cybersecurity, financial intelligence, or political risk analysis.
- Agility and Adaptability: Private firms are typically more agile and adaptable than government agencies, allowing them to respond quickly to evolving threats and opportunities.
- Cost-Effectiveness: Private firms can offer cost-effective solutions for intelligence gathering, particularly for businesses and individuals who may not have the resources to establish their own in-house intelligence capabilities.
6. The Ethical Challenges of Espionage:
The increasing sophistication of espionage techniques raises significant ethical concerns, particularly in the realm of cyberespionage. The potential for misuse and abuse of technology is a constant concern, as is the need to balance national security interests with individual privacy and civil liberties.
Ethical Considerations in 2025:
- Privacy Invasion: The use of surveillance technology, including facial recognition and data mining, raises serious concerns about privacy invasion and the potential for misuse of personal information.
- Cyber Warfare and Espionage: The blurring lines between cyber warfare and espionage raises ethical questions about the use of offensive cyber operations and the potential for escalation of conflict.
- Transparency and Accountability: There is a growing need for transparency and accountability in the use of espionage techniques, particularly by governments and private intelligence firms.
7. The Importance of Counterespionage:
As espionage becomes more sophisticated, the need for effective counterespionage measures becomes increasingly critical. Counterespionage aims to protect individuals, organizations, and nations from espionage activities by identifying and neutralizing threats.
Key Aspects of Counterespionage in 2025:
- Threat Assessment and Risk Management: Identifying potential threats and developing strategies to mitigate risks is crucial for effective counterespionage.
- Cybersecurity and Data Protection: Strengthening cybersecurity defenses and implementing data protection measures is essential to prevent cyberespionage attacks.
- Personnel Security and Background Checks: Rigorous background checks and security measures are necessary to prevent the recruitment of individuals by foreign intelligence agencies.
8. The Future of Espionage:
The trends outlined above suggest that espionage will continue to evolve rapidly in the coming years. Technological advancements will continue to drive innovation in intelligence gathering, while the geopolitical landscape will shape the focus and priorities of espionage activities.
Emerging Technologies and Their Impact:
- Quantum Computing: Quantum computing has the potential to revolutionize cryptography, making current encryption methods obsolete. This could lead to new challenges for espionage, both in terms of protecting sensitive information and exploiting vulnerabilities in existing systems.
- Biometric Technologies: Biometric technologies, such as facial recognition and iris scanning, are becoming increasingly sophisticated and widely used. This raises concerns about the potential for misuse in espionage, as well as the need for robust privacy protections.
- Neuroscience and Brain-Computer Interfaces: Advancements in neuroscience and brain-computer interfaces could potentially be used to extract information from individuals without their knowledge or consent, raising serious ethical concerns.
Geopolitical Factors and Their Influence:
- Great Power Competition: The resurgence of great power competition between the United States, China, and Russia will likely drive increased espionage activities, as each country seeks to gain an advantage over its rivals.
- Cybersecurity Threats: The growing threat of cyberattacks from state and non-state actors will lead to increased focus on cybersecurity and counterespionage measures.
- The Rise of Non-State Actors: Non-state actors, such as terrorist groups and organized crime syndicates, are increasingly sophisticated in their use of technology and intelligence gathering. This will require a more comprehensive approach to counterespionage, including cooperation between governments and private organizations.
Related Searches:
1. Cyberespionage Techniques: This search explores the methods used by cyberespionage actors, including malware, phishing, social engineering, and denial-of-service attacks.
2. Counterespionage Strategies: This search examines the tactics and techniques used to protect against espionage, including threat assessment, cybersecurity, and personnel security.
3. The Role of Technology in Espionage: This search investigates the impact of technological advancements on espionage, including the use of artificial intelligence, quantum computing, and biometrics.
4. Espionage in the 21st Century: This search examines the changing landscape of espionage in the digital age, focusing on the rise of cyberespionage, the convergence of physical and cyber operations, and the increasing role of private intelligence firms.
5. Ethical Concerns in Espionage: This search explores the ethical implications of espionage, including privacy invasion, the potential for misuse of technology, and the need for transparency and accountability.
6. The Future of Espionage: This search examines the emerging trends and technologies that are shaping the future of espionage, including the impact of quantum computing, artificial intelligence, and biometrics.
7. Famous Espionage Cases: This search explores notable historical cases of espionage, providing insights into the motivations, methods, and consequences of espionage activities.
8. The History of Espionage: This search delves into the history of espionage, tracing its evolution from ancient times to the present day.
FAQs:
1. What are the most common cyberespionage techniques used today?
Common cyberespionage techniques include:
- Malware: Malicious software designed to steal data, disrupt operations, or provide remote access to target systems.
- Phishing: Tricking individuals into revealing sensitive information by posing as a legitimate entity.
- Social Engineering: Manipulating individuals into providing information or access to systems through psychological tactics.
- Denial-of-Service Attacks: Overloading target systems with traffic, rendering them unavailable to legitimate users.
2. How can individuals protect themselves from cyberespionage?
Individuals can protect themselves from cyberespionage by following these best practices:
- Use Strong Passwords: Create unique and strong passwords for all online accounts.
- Be Cautious of Phishing Attempts: Be wary of suspicious emails, links, and attachments.
- Keep Software Updated: Install security updates for operating systems and software to patch vulnerabilities.
- Use Antivirus and Anti-Malware Software: Install and regularly update antivirus and anti-malware software to protect against threats.
- Enable Two-Factor Authentication: Enable two-factor authentication for important accounts to add an extra layer of security.
3. What is the role of counterespionage in protecting national security?
Counterespionage plays a crucial role in protecting national security by:
- Identifying and Neutralizing Threats: Counterespionage agencies work to identify and neutralize foreign intelligence operatives and their activities.
- Protecting Sensitive Information: Counterespionage efforts aim to prevent the theft of classified information and sensitive data.
- Maintaining National Security: Counterespionage helps to protect national security by preventing foreign interference in domestic affairs and protecting critical infrastructure.
4. What are the ethical challenges of using advanced technologies in espionage?
The use of advanced technologies in espionage raises a number of ethical challenges, including:
- Privacy Invasion: Surveillance technologies, such as facial recognition and data mining, raise serious concerns about privacy invasion.
- Misuse of Technology: There is a potential for misuse of technology in espionage, including the targeting of individuals or groups for political or personal reasons.
- Transparency and Accountability: There is a need for transparency and accountability in the use of espionage technologies, particularly by governments and private intelligence firms.
Tips:
- Stay Informed: Stay informed about the latest trends in espionage and cybersecurity to understand the evolving nature of threats.
- Enhance Cybersecurity: Implement robust cybersecurity measures to protect your organization or personal information from cyberespionage attacks.
- Be Vigilant: Be vigilant about potential espionage activities, including suspicious individuals, unusual behavior, and attempts to access sensitive information.
- Report Suspicious Activity: Report any suspicious activity to the appropriate authorities, such as law enforcement or intelligence agencies.
Conclusion:
The landscape of espionage is constantly evolving, driven by technological advancements, shifting geopolitical realities, and the ongoing pursuit of information. Understanding the key trends in espionage is crucial for individuals, businesses, and governments alike, as it provides insights into the evolving nature of threats and opportunities in the digital age.
As we move towards 2025, cyberespionage will continue to dominate, with sophisticated attacks targeting critical infrastructure, financial institutions, and government agencies. The convergence of physical and cyber espionage will become increasingly common, blurring the lines between the two domains. While technology plays a crucial role in intelligence gathering, human intelligence (HUMINT) remains a critical component, providing context and deeper understanding to data gathered through cyber means. Open source intelligence (OSINT) will continue to grow in importance, leveraging the vast amount of data available online to gather actionable intelligence.
The ethical challenges of espionage will continue to be a major concern, particularly in the realm of cyberespionage. The potential for misuse and abuse of technology is a constant concern, as is the need to balance national security interests with individual privacy and civil liberties. Effective counterespionage measures will become increasingly critical as espionage techniques become more sophisticated.
The future of espionage will be shaped by emerging technologies, such as quantum computing, biometrics, and neuroscience, as well as by evolving geopolitical realities. Understanding the trends in espionage and the ethical challenges they present is essential for navigating the complexities of the digital age.

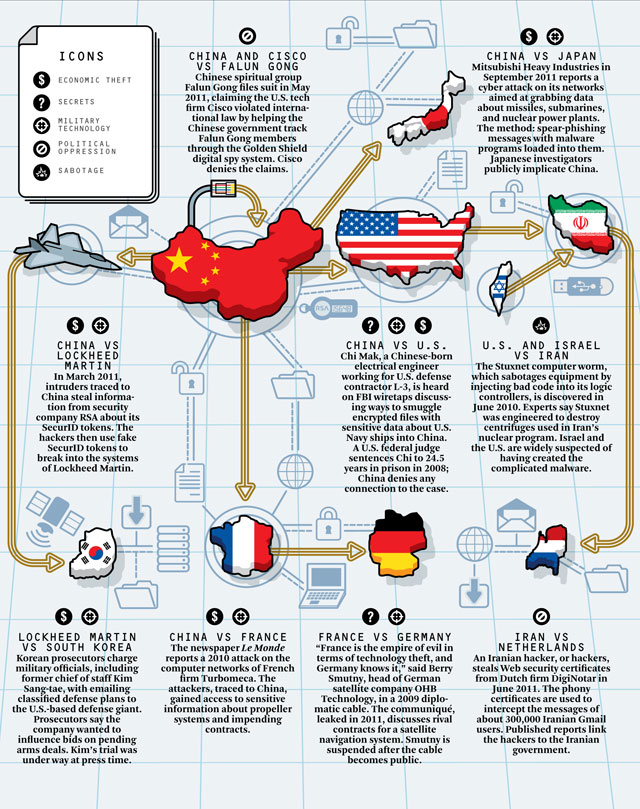





Closure
Thus, we hope this article has provided valuable insights into The Evolving Landscape of Espionage: Spy Trends 2025. We appreciate your attention to our article. See you in our next article!